Blog
How to Implement User Authentication Securely in a Staff Attendance App
- May 15, 2025
- 10:54 am
As more companies digitize their employee management systems, the importance of protecting user data continues to grow. A major component of this is the implementation of secure user authentication within staff attendance applications. With robust security measures in place, businesses can safeguard confidential data, prevent breaches, and ensure the system’s reliability.
This article outlines essential techniques and best practices to effectively integrate secure authentication into your staff attendance solution.
Importance of Secure Authentication
Strong authentication methods are essential for ensuring:
- Protection of employee records
- Accurate time tracking and payroll
- Reduced risk of security breaches and regulatory issues
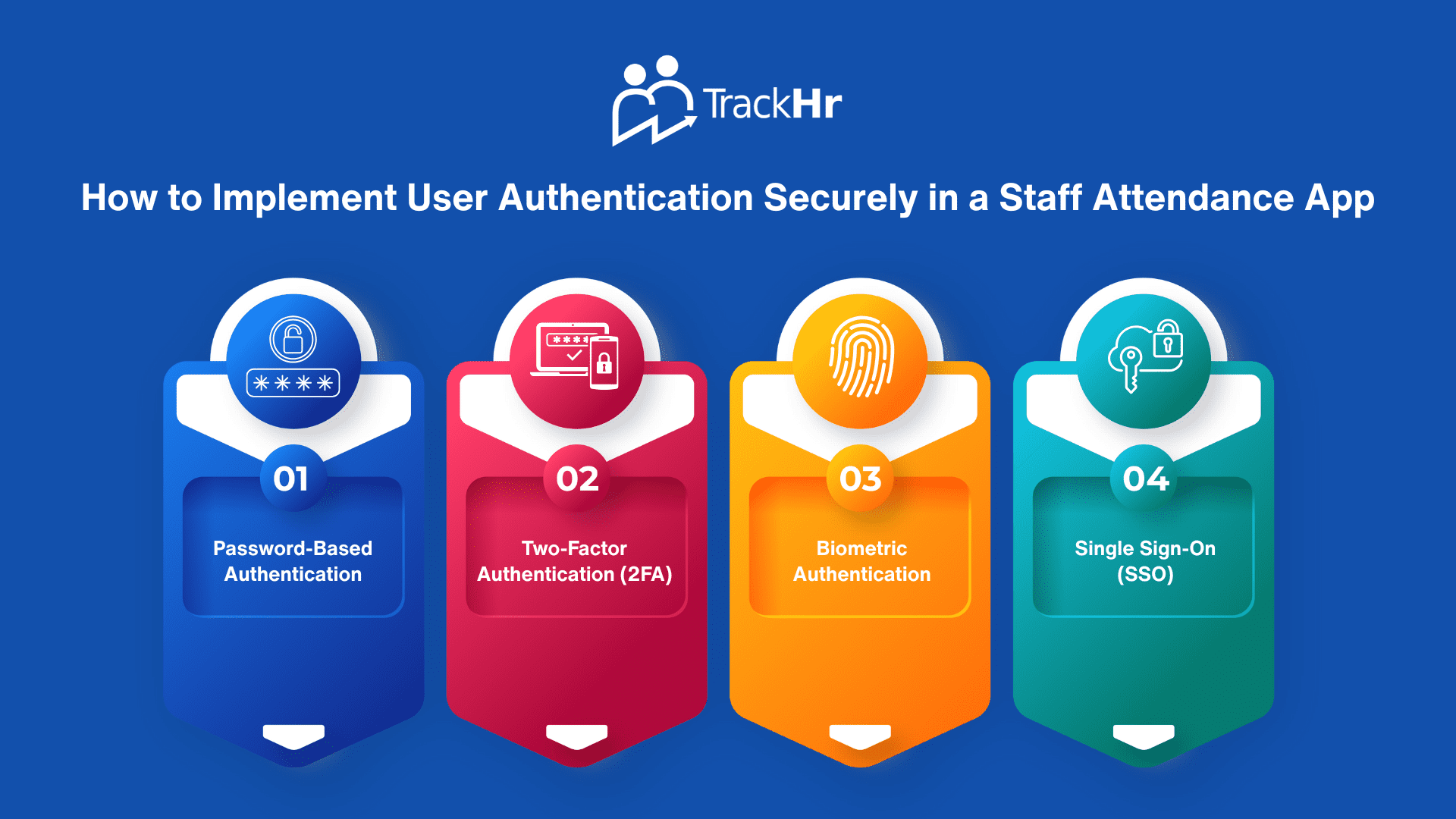
Core Authentication Techniques
1. Password-Based Authentication
Traditional yet widely used, password authentication can be enhanced through:
- Enforcing complex password policies
- Requiring regular password updates
- Implementing secure password storage using hashing algorithms like bcrypt
2. Two-Factor Authentication (2FA)
2FA strengthens security by requiring a second verification step, such as:
- One-time passwords (OTP) via SMS or email
- Verification through an authenticator app
3. Biometric Authentication
Biometric systems such as fingerprint or facial recognition are especially useful in mobile apps.
Advantages:
- Hard to replicate
- Fast and user-friendly
4. Single Sign-On (SSO)
SSO allows users to access multiple integrated systems with one login.
Ideal For:
- Businesses with interconnected applications
- Users managing multiple access points
Recommended Security Practices
Encrypt User Data
Utilize modern encryption methods to secure stored and transmitted data.
Rate Limiting and Account Lockouts
Protect against brute-force attacks by limiting login attempts and triggering lockouts after multiple failures.
HTTPS for Secure Communication
Ensure data is encrypted during transmission using SSL/TLS protocols.
Regular Testing and Audits
Perform security assessments regularly to detect and resolve vulnerabilities.
Proper Session Handling
Use session timeouts and secure token management to prevent unauthorized access.
Tools and Technologies
Ensure data is encrypted during transmission using SSL/TLS protocols.
- Firebase Authentication – Quick integration and multiple authentication options
- Auth0 – Customizable identity and access management
- OAuth 2.0 / OpenID Connect – Standard protocols for secure authorization
Legal and Regulatory Compliance
Ensure your application meets regional data security standards:
- GDPR (EU)
- HIPAA (U.S. health data)
- CCPA (California privacy)
Compliance helps avoid fines and builds trust with users.
Conclusion
Secure user authentication is a crucial part of any staff attendance application. By integrating multi-layered authentication methods and adhering to best practices in cybersecurity, your system can remain robust, reliable, and compliant. Ongoing updates and proactive security strategies are essential to stay ahead of evolving digital threats.
Table of Contents
Exhausted from managing performance management manually?